Assess and value what information should be created to support your agency’s business and regulatory requirements.
To do this, consider your agency's:
- legal and regulatory requirements
- associated risks and
- business objectives.
Identify and manage risks associated with not creating information to support requirements.
Relationship to the Information Management Standard
The Information Management Standard requires that Information assets must be managed appropriately.
To do this, it is vital to understand how your agency’s information assets support business objectives and operations, including compliance obligations (Behaviour 1.2).
This helps determine their value. Linking information assets back to your agency’s business functions and activities will enable this understanding (Behaviour 1.3).
In addition to the information assets identified through the audit, you also need to analyse and document the information your agency needs to create to meet its legal and operational obligations (Behaviour 2.1).
All information assets created must be complete and accurate appropriate to your agency’s business processes, regulatory environment and risk and accountability requirements.
This is achieved by conducting a value and risk assessment in accordance with your agency’s risk management framework. Risks associated with not creating the required information must also be identified and managed (Behaviour 2.3).
Why assess value and risk?
By knowing what information assets are held it is possible to assess:
- the value of those assets,
- the risks to those assets and
- any action that might be needed to manage and protect them from compromise (compromise includes, but is not limited to, loss, misuse, interference, unauthorised modification, unauthorised disclosure), and
- how those assets support business objectives, as well as operations and compliance obligations.
Assessing value and risk relies on a good understanding of your agency’s external and internal context. External and internal context can be determined through a business and regulatory analysis.
- external context includes:
- regulatory requirements
- political and societal influences
- economic environment
- technological and physical environment, and
- contractual relationships.
Information assets that may not be of high value to your agency but may be to the State of South Australia and need to be permanently retained.
- internal context includes:
- governance and organisational structure
- policies, objectives and strategies
- resources, capabilities or knowledge
- decision-making processes
- technological environment
- standards and guidelines adopted by your agency, and
- contractual relationships.
This includes the business context in which the information assets are being created and used and any governance arrangements in place addressing the management (both administrative and regulatory), and registration of its information.
Understanding your agency’s organisational, accountability and regulatory requirements means priorities can be determined based on objective data, which in turn enables planning of information related actions and justifiable allocation of resources.
Regardless of the value of an information asset, it cannot be disposed of unless authorised under a current disposal schedule. Any disposal action must be part of an authorised information management program and with the authority of the appropriate information management practitioner.
How to determine the value of information
‘Value’ is the level to which something is held to be important, worthy, or useful. In relation to information assets, ‘value’ can mean a monetary amount but also includes the value the asset has in its business, legal, political or social context.
There are two angles from which to value an information asset under the State Records Act 1997 (SR Act):
- its present importance to your agency, the government and the community, acknowledging this might change over time
- its ongoing value to the State as an authoritative source of evidence, summary of substantive decisions or actions, or aesthetic or historical significance (which would be deemed to be permanent under the Appraisal Standard).
High value information assets are those that enable the performance of your agency’s functions, to provide services and may be of permanent value either to your agency, government and / or wider society.
Information assets with an active business value, but not necessarily of permanent value, are critical in enabling your agency to:
- undertake and continue your functions
- make good decisions
- service your clients / customers
- maintain or enhance your reputation
- respond to commissions, inquiries, audits, investigations and legal issues.
State Records’ Appraisal Standard outlines the criteria for determining information assets of permanent value to the South Australian government.
Note: Regardless of the value of an information asset, it cannot be dispose of unless authorised under a current disposal schedule and any disposal action must be part of an authorised information management program and with the authority of the appropriate information management practitioner.
Deciding information assets to make or keep
The process of deciding what information assets should be made and kept, based on value and risk, is also known as appraisal (refer to the Appraisal Standard).
This is different from an information asset audit which records what information assets your agency has, not what it should be creating or keeping.
Appraisal is achieved by:
- gathering information about the relevant business activity or process, including the people involved in the process (customers, clients, citizens)
- analysing the broader legislative, political and social context of the business
- documenting the value and risk assessment to communicate and account for the decisions.
Consider the following sources to help identify your agency’s information needs:
- legislation and regulations
- business activities and functions (for example services provided to customers)
- industry and State Records standards
- government policies and procedures
- audit reports (for example Auditor-General, other external or internal audit reports conducted on, and or by, your agency)
- business impact assessments
- Ombudsman reports
- Royal Commission reports or relevant inquiries or reviews
- MOUs
- community and customer expectations.
These sources articulate specific information assets to be created, kept or provided. For example, under Regulation 425 of the Work Health and Safety Regulations 2012, your agency must create and maintain an asbestos register.
Where information requirements are not clear in legislation or regulations, it may be necessary to seek legal advice. For more information on appraisal refer to State Records’ Appraisal Standard or ISO TR 21946 Information and documentation – Appraisal for Managing Records.
Your agency must identify and include in any contracts with third party providers who provide services on behalf of the government any legal requirements to create and keep information assets. Refer to the Contracting Standard for more information.
Business classification
Once your agency’s information requirements (what it should be creating) have been identified, these should be linked back to business functions and activities. This can be documented using a classification scheme (Behaviour 1.3).
A classification scheme applies a uniform hierarchical set of terms and conventions to classify, title and retrieve information assets.
Benefits of classification include:
- consistency in the description of information assets
- documenting the link between information assets and business activities and functions
- documenting access and security decisions (for state government agencies these decisions must be made and documented in accordance with the South Australian Protective Security Framework (SAPSF) and South Australian Cyber Security Framework (SACSF)
- improving the accuracy and ease of retrieval
- assisting in sentencing and disposal of information assets.
There may be information assets that you are unable to link to your current functions and activities, for example information assets of defunct or predecessor agencies. For the management of these assets, please contact State Records.
Gap analysis
Once your agency’s information requirements have been identified this can be compared against the information your agency already creates.
Gaps, as risks, can be added to an information assets risk assessment, to be managed and mitigated.
Value changes over time
The value of most information assets will change over time.
How the value of an information asset changes over time will depend on several factors, including the potential use of an asset beyond its original purpose, your agency’s organisational, accountability and regulatory requirements and potential societal changes. For example:
- high value information assets may decline as the risk for your agency and the community passes. A contract is high value while it is active, then decreases in value after the contract has finished but it still holds some value in case of any recourse. It then becomes of low or no value once the time has expired for recourse. The value scale will depend on what the contract is for. Contracts for major building works would have a longer value over time in comparison with a short-term cleaning contract.
- permanent value information assets, either to your agency or the State, may retain their high value indefinitely, even as their use changes. School registers or hospital admissions are high value to particular agencies as evidence of the delivery of services. Over time, these registers offer evidence of family relocations and familial or societal health trends.
- information assets of little or low value to the business may become high value to the community. An agency visitor sign in sheet needed for security or safety on a given day, may become relevant in an Inquiry as evidence of who was on site on a particular time or date.
- evidence needed for reporting diminishes once reports have been made. Accounting spreadsheets might have medium value for a finite period then reduce to low or no value once regulatory requirements have been met. They may be duplicated for future reporting cycles but are only for reference. If they were lost, the impact would be low.
How to assess level of risk
‘Risk’ is the effect of uncertainty. It is a deviation from the expected, which can be positive or negative.
Risks are analysed in terms of potential events, the likelihood of those events and the consequences of those events both internally and externally.
All risks to your agency should be identified, assessed and managed according to your agency’s risk management framework and risk management processes.
For more information on risk assessments refer to your agency’s risk management policies or the ISO TR 21946 Information and documentation – Appraisal for Managing Records.
Types of risk
While there are many different types of risk to your agency, the two information-related risks are:
- business risk: not having, or not being able to find, the information needed to meet your agency’s obligations or the inappropriate disclosure of information through inadequate security or privacy management. For example:
- staff employment agreements are visible to a range of unauthorised staff within a corporate records management system, or
- documentation of a major tender process is not available to query a breach of contract.
These risks can be mitigated by having an information asset register and knowing your agency’s information requirements.
- risk to the information assets themselves: through:
- inadvertent deletion
- poor physical storage or inadequate digital backup
- incident / disaster
- theft
- ransomware or other cyber attacks, or
- corruption.
Identification of potential events
Any risk event or circumstance that could affect business objectives and compliance obligations needs to be identified.
Initially this can be done based on past failures and successes, customer complaints, legal matters your agency has been involved in, watchdog reports, historical research or other events.
The causes and sources of the risk can also be discovered through questionnaires, interviews, review of complaints received, workshops, examples from other agencies or testing scenarios.
In assessing the level of risk to an information asset or assets, consider:
- what is the impact or consequence on the business of information not existing, or being unable to be found when required?
- what is the likelihood of the information being needed for any purpose?
- does this likelihood diminish over time?
- does the impact, effect and cost of remediation reduce over time?
- what are the physical or digital risks to the information assets themselves?
Table 1 provides some examples of risks to information assets.
Table 1: Risk examples
| Potential source of risk | Examples |
|---|---|
| Changes in the external environment |
|
| Changes in the internal environment |
|
| Adequacy of the systems that manage information assets |
|
| Processes for managing the information assets |
|
Likelihood of the event
Once the potential event is known, consider the expected likelihood (probability or frequency) of that event occurring. For example:
- is a system outage a rare occurrence, or does it happen regularly?
- are physical security breaches increasing around the offsite storage or transport of hardcopy information?
Likelihood is usually quantified on a scale, ranging from ‘remote’ likelihood to ‘almost certain’.
Each risk should be assessed in terms of the likelihood of an event happening and the consequence if it does happen.
Potential consequences and impact
Poor information management results in:
- loss of evidence of a business transition or decision because it was never created or retained
- information assets being lost or damaged, destroyed, incomplete or inaccessible
- unauthorised access, breaching security and privacy
- altered information which is unable to be trusted.
These results might have an impact on business objectives and compliance requirements.
Table 2 expands on the potential consequences of poor information management.
Table 2: Potential consequences
| Potential consequence | Examples of impact |
|---|---|
| Ethical |
|
| Cultural |
|
| Legal |
|
| Social |
|
| Reputational |
|
| Environmental |
|
| Financial |
|
Agencies must formally notify State Records of any lost or misplaced information assets as soon as possible after an incident has occurred.
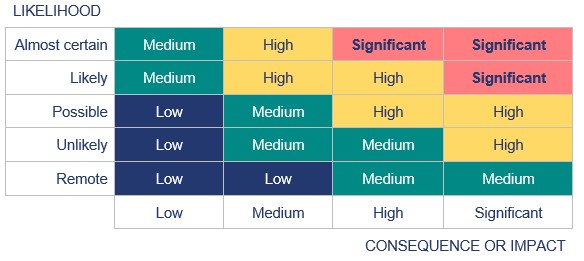
Rating the risks
One example of a consequence / likelihood matrix is below using a five-point likelihood scale and a four-point consequence scale.
Placing a risk event in any of the squares determines its significance and therefore the urgency for action to address the risk.
For example, an external cyber infiltration event may result in information being lost or compromised. This could halt some operations and expose other systems to disruption. This event’s likelihood is ‘possible’ but has ‘high’ consequences. The risk therefore falls into a category of ‘high’ significance and urgency for action.
Like value, the level of risk can change over time, so a risk assessment should be revisited periodically to ensure that risk mitigation measures remain fit for purpose.
Table 3: Example four-point consequence scale
All risks should be recorded as part of your agency’s risk management program, whether in a separate information risk register or within a general agency-wide risk register or program.
Outcomes from assessing value and risk
Identifying information assets that are of high value and / or are at high risk enables priorities to be determined, strategies and plans to be developed and resources to be allocated accordingly.
Using a value-risk matrix can give an indication of where to assign priorities for risk treatment or mitigation.
Table 4: Example value-risk matrix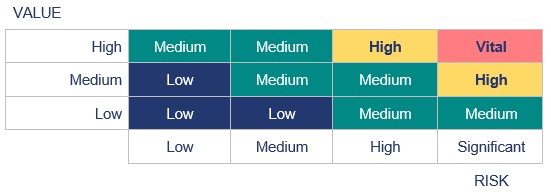
These priorities will form the foundation of the Information Management Plan by enabling your agency to:
- identify and manage associated risks of not creating or managing information required for business activities and compliance
- prioritise efforts or resourcing
- help meet compliance with regulatory requirements for information assets (such as the SR Act, Freedom of Information Act 1991, Public Sector (Data Sharing) Act 2016, open access directives, etc
- determine protection measures for information as required to maintain the security, confidentiality, privacy, integrity and availability of the information assets, including the assignment of physical, personnel, digital and information classification controls
- develop business continuity programs and incident recovery plans
- support the development of a disposal schedule
- develop strategies and prioritise investment to ensure information assets remain in a usable and readable format for as long as required (for example through preservation or mitigation)
- identify any 'silos' of information and decide what (if any) action to take. For example locating the information asset elsewhere, opening access to other areas of your agency, other areas of government or the public
- identify where using existing information assets can be used to a greater extent, to reduce duplication of systems or effort
- develop mechanisms for greater discoverability to support, for example, subpoena and other legal discovery processes.

